|
In our work with large customers over the past four years, we repeatedly heard several things:
"We know that we need to embrace AJAX technology, but we're struggling with decisions on architecture and how to prioritize our efforts to achieve the maximum business return."
"We don't have internal staff with the training or, more importantly, the experience in deploying AJAX, SOA, and other new technologies within Web-enabled applications."
"The applications that could really benefit from the increased usability of AJAX are highly mission-critical to us - so we're very concerned with the risk of implementing new technologies like AJAX."
Today, you can buy AJAX widget libraries and development toolkits from dozens of vendors. But AJAX technology by itself can't address any of the very real issues listed above. That's why JackBe has responded with a total solution approach that we think you'll find refreshing and clearly different. Instead of simply shipping you a bunch of products and leaving you on your own to succeed or fail, we create a customized package that includes everything you need to ensure your AJAX success with minimal risk:
In-depth expertise and experience from a pioneer in the AJAX space - we were delivering rich internet applications with our technology years before the term 'AJAX' even existed!
Intellectual property and methodologies created and refined during over 30 AJAX implementations within mission-critical applications for industry-leading enterprises
UniTargetSoft proven and highly respected AJAX visual development and deployment platform
Comprehensive services offerings to help your enterprise at every stage of the application life cycle.
This 'total solution' approach eliminates risk, guarantees results, minimizes time-to-market, maximizes the benefits of AJAX technology, and rapidly improves usability without a 'rip and replace' of your entire application.
Schematic Representation of Development
Approach Development Life
Cycle
 |
Describes end-of-system activities.
Emphasis is given to proper preservation of data. |
 |
Describes tasks to operate and maintain
information systems in a production environment, includes Post Implementation
and In-Process Reviews. |
 |
Includes implementation preparation,
implementation of the system into a production environment, and resolution of
problems identified in the Integration and Test Phase. |
 |
Demonstrates that the developed system
conforms to requirements as specified in the Functional Requirements Document.
Conducted by Quality Assurance staff and users. Produces Test Analysis
Reports. |
 |
Converts a design into a complete
information system. Includes acquiring and installing systems environment;
creating and testing databases/ preparing test case procedures; preparing test
files; coding, compiling, refining programs; performing test readiness review
and procurement activities. |
 |
Transforms detailed requirements into
complete, Detailed System Design Document. Focused on how to deliver the
required functionality. |
 |
Analyzes user needs and develops user
requirements Creates a detailed functional Requirements
Documents |
 |
Develops a Project Management Plan and
other planning documents. Provides the basis for acquiring the resources need to
achieve a solution. |
 |
Define the scope or boundary of the
concepts Includes Systems Boundary Document, Cost Benefit Analysis, Risk
Management Plan and Feasibility Study |
 |
Begins when a sponsor identifies a need or
an opportunity. Concept Proposal is
created |
|
Schematic Representation of QA Approach
|
|
|
|
Configuration Management & Data Recovery
|
|
The staying power of any software engineering organization in today's world is
directly related to its commitment to strong software configuration management
practices, its communication effectiveness through documentation, and its
adherence to accepted software engineering standards.
UniTargetSoft believes that a clear and continually updated definition of requirements
is a major cause of our project success. As a result, requirements management
is recognized as vital to companies that rely more and more on software for
conducting business and mission-critical functions.
UniTargetSoft follows a streamlined change lifecycle with process-based change
management solutions. Policy-based configuration management solutions that
automate the packaging, configuration, provisioning and repair of software,
results in a configuration management that ensures the orderly release and
implementation of new/revised software and related documentation. We implement
only approved changes to both new and existing software, and we verify that
software changes comply with approved specifications. We execute changes and
updates in project documentation and make sure that the changes are visible to
project management. By evaluating and communicating the impact of changes, we
prevent unauthorized changes from being made.
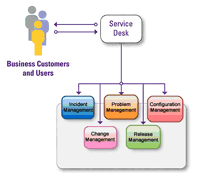
Our Incident and Problem Management provides a focal point for recording
incidents, assessing their impact, prioritizing, classifying, routing, and
escalating them, and tracking them through to their resolution. Our source
codes are centralized to a configuration library audited on periodical basis.
Our servers are equipped with redundancy settings for speedy recovery in case
of disaster.
|
 |
